Today we tackle our most controversial topic date: the question of whether a backdoor exist in MH370’s satcom system that would have allowed the BFO data to be tampered with. If so, it will have radical implications for what might have happened to the plane.
Back in Episode 7 we explained how the BFO data worked and how it showed conclusively that the plane must have gone south. But then some strange facts started to appear that, taken together, suggested that all might not be as it seemed.
The first was that, as we’ve discussed earlier, the Satellite Data Unit had been turned off and back on again. Officials didn’t let that slip until June 26. Up until that time, we’d all assumed that the satcom had inadvertantly been left on when everything else was turned off. The fact that it was turned on was really hard to explain. In fact to this day, people have had a hard time coming up with a convincing reason why anyone would either know how to do this or want to do this. I hasten to add that is a hugely contentious point. Some people say they have perfectly good explanations, but they all seem pretty daft to me. For instance, Victor Iannello thinks it was done in order to prevent someone in the cabin from using the satphone to call for help, but there are simpler ways to turn off the satphone.
The second surprising fact to emerge was that it turned out that the electronics bay, or E/E bay, the compartment that houses all of the computers that control the plane, is accessible through a hatch in the first-class cabin.
Matt Wuillemin, an Australian former 777 pilot, wrote a master’s thesis on the security vulnerability of the unlocked hatch in June 2013. In his thesis, Wuillemin notes that in addition to the Flight Control Computers, the E/E bay also houses the oxygen cylinders that supply the flight crews’ masks in case of a depressurization event, and the controls for the system that locks the flight deck door. “Information is publicly available online describing the cockpit defences and systems located within this compartment,” Wuillemin notes. “This hatch may therefore be accessible inflight to a knowledgeable and malevolent passenger with catastrophic consequences.”
The last piece of the puzzle fell into place when Jeff had a conversation with an influential independent reseracher named Mike Exner. He had asked Mike how the Satellite Data Unit gets the navigational information that it needs to calculate the Doppler precomposition that produces the BFO. Exner replied that it comes through a cable from a unit called the IRS (Inertial Reference System) that’s in the electonics bay.
If you climbed down into the E/E bay and disconnected the SDU cable from the IRS, you could plug it into an electronic device capable of generating false position information. Such gear would have to be manufactured from scratch; “there are certainly no commercial, off-the-shelf boxes like that,” said Exner. In essence, the signal would be lying to the SDU about where the plane was located and how fast it was going, causing the SDU to transmit at an incorrect frequency.
Later, Victor Iannello developed this idea even further. He pointed out that if you changed just one parameter inside the SDU, you would create BFO values that would make the plane look like it was going south when it was really going north. He wrote a paper exploring the idea that you can find here.
Two important points:
a) We don’t know definitely that this vulnerability truly exists. There may be some aspect to the 777’s electronics that we don’t know about that would rule this out. One of the interviewees in the Netflix documentary says that you can’t take over the controls of a 777 from the electronics bay. Others have made the same claim. I don’t know how they would know this, and no one has explained so far, but it’s possible they’re right.
b) Victor later became convinced by other evidence that the vulnerability, even if it did exist, was not used.
But! The mere possibility that the data could have been tampered with to create what amounted to a false tale of breadcrumbs was breathtaking.
Remember: at the time, the authorities were getting ready to launch an incredibly ambitious search of the remote ocean seabed based at this point solely on the basis of a handful of signals the likes of which no plane had ever transmitted before, whose origin they couldn’t explain, and whose meaning they couldn’t verify by any means, whether satellite photos, radar returns, floating debris, or anything else.
Everything was hanging on these signals which everyone just assumed had been produced innocently and inadvertently, with no intention on anyone’s part.
What we’d discovered was that that wasn’t necessarily true. There was another way to create these signals. So now, as Jeff saw it, we’d have to put an asterisk next to every instance where someone says, “We know the plane went into the southern Indian Ocean.” Beause there is another way to interpret that data.
And here’s something else to consider.
For this exploit to have been possible, a whole bunch of things had to line up.
The hijacked plane would have to be a Boeing, not an Airbus. It would have to be a fly-by-wire 777 or a 787, not one of Boeing’s earlier planes which used mechanical rather than electronic control systems. The airline would have to be subscribing to the low-cost version of Inmarsat’s service, called Classic Aero, and not its high-end version, Swift Broadband. Its route after disappearing would have to have been entirely under the footprint of an aging Inmarsat satellite in a decaying orbit. And the implied direction would have to be toward an oceanic basin in which the plane could be “lost.” And the mirror routes to discriminate would have to lie on a north-south axis.
MH370 meets all these criteria.
Grant you, if this hack were carried out it would involved some incredibly sophisticated perps. But not unthinkably so. If you work in the field of electronic warfare (EW), the idea of changing the apparent Doppler shift of a signal is used all the time. (As I discussed in a recent article about UAP sightings and EW for New York magazine.) So for some people, this kind of idea wouldn’t be that wacky at all.
Now, not many people understand how this vulnerability works; a lot of people don’t get past the words “Doppler Precompensation.” And of the ones who do, a great many find it preposterous that this vulnerability was exploited.
But no one, to our knowledge, has demonstrated that it is impossible. And that means that there’s a whole alternate lens that you can use to look at the disappearance of MH370.
Things that seem to be random or to have occurred just by chance, like the reboot of the SDU, now seem to have a very specific purpose.
Anyway, by the end of June, 2014, Jeff was starting to wonder if the whole world had gotten MH370 fundamentally wrong.
And he thought that the answer to that question would emerge pretty soon. Because a seabed search was about to start, and the if the vulnerability had been exploited, then it would leave a very specific clue:
The plane’s wreckage would not be found on the seabed floor where the BFO data suggested it had gone.
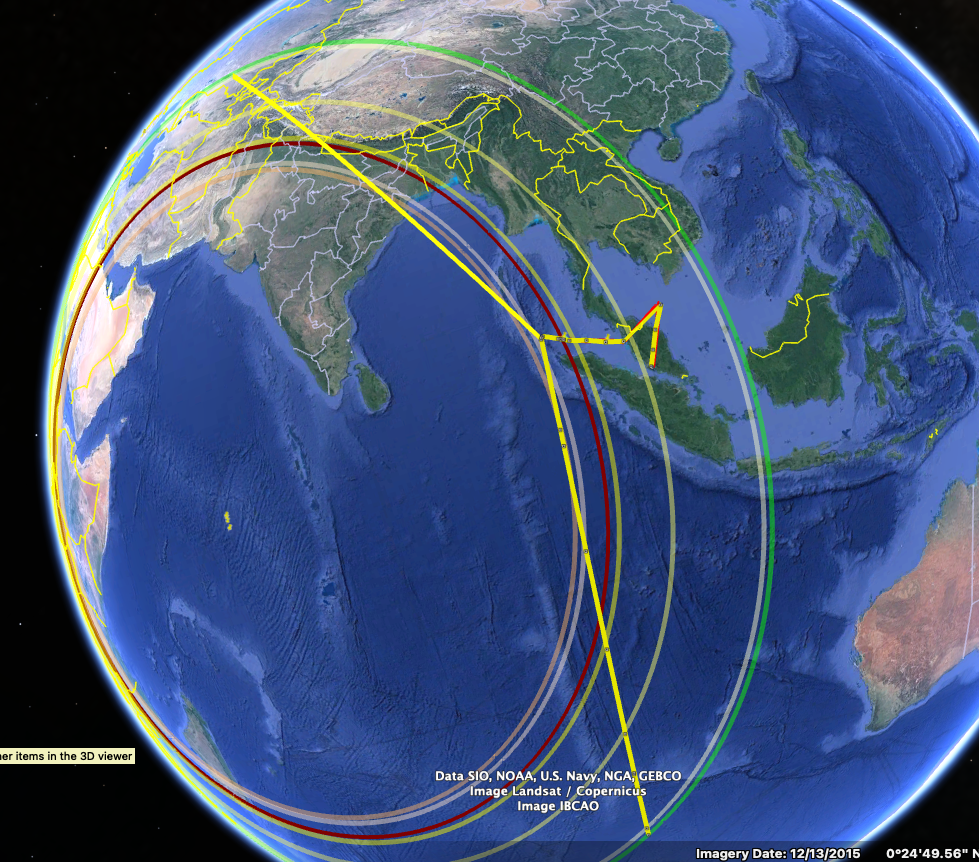
The Burst Timing Offset (BTO) component of the Inmarsat data suggested that the plane either flew south into the remote Indian Ocean or north to Kazakhstan.
To watch Deep Dive: MH370 on YouTube, click the image above. To listen on Apple Music, click here. It’s also now available on most other podcast platforms as well, including Spotify.